Industrial network
It is suitable for industrial Internet 5G wireless connections, such as data transparent transmission of various devices, industrial protocol conversion, and mutual control of devices.
Industrial Cyber Security
- Categories:工业网络
- Time of issue:2021-11-09 13:25:22
- Views:0
With the integration of industrialization and the rapid development of the Internet of Things, industrial control systems such as SCADA, DCS, PLC, which are widely used in my country's key infrastructure and energy industries, increasingly use computer and network technologies, such as Ethernet TCP/IP and OPC, etc. , which greatly promotes industrial production, but also makes the interface of industrial control system more and more open, and the information security problem faced by control system is also becoming more and more serious.
ICS system security incidents in industrial environments different from traditional IT information security can lead to:
1. Key performance drops, affecting system availability
2. Key control data is tampered with or lost
3. Loss of control
4. Environmental disaster
5. Casualties
6. Damage to the company's reputation
7. Crisis public life and national security
8. Destruction of infrastructure
9. Serious economic losses, etc.
Industrial information security is becoming more and more important, and various potential security threats are also growing, such as illegal access by unauthorized personnel, espionage, illegal manipulation of control data, data loss and damage due to malicious software, etc. A growing number of security incidents reveal security vulnerabilities in automated factories.
Industrial control system information security (hereinafter referred to as "industrial control security") is an important part of national network and information security, and is the basic guarantee for promoting Made in China 2025 and the integrated development of manufacturing and the Internet. In order to implement the spirit of the document "Guiding Opinions of the State Council on Deepening the Integrated Development of Manufacturing and the Internet" (Guo Fa [2016] No. 28), respond to the industrial control security situation in the new era, and improve the industrial control security protection level of industrial enterprises. In October 2016, the Ministry of Industry and Information Technology issued the "Guidelines for Information Security Protection of Industrial Control Systems". In May 2017, the Cybersecurity Law was officially implemented.
工业信息安全不单纯是一个技术问题,而是从一个意识培养开始,涉及到管理,流程,架构,技术,产品等各个方面的系统化的工程分为4个阶段
1、风险评估
2 、安全策略与组织审核
3 、技术措施
4、验证与改进
依据工业和信息化部印发《工业控制系统信息安全防护指南》,工业控制系统信息安全是国家网络和信息安全的重要组成部分,是推动中国制造2025制造业与互联网融合发展的基础保障。
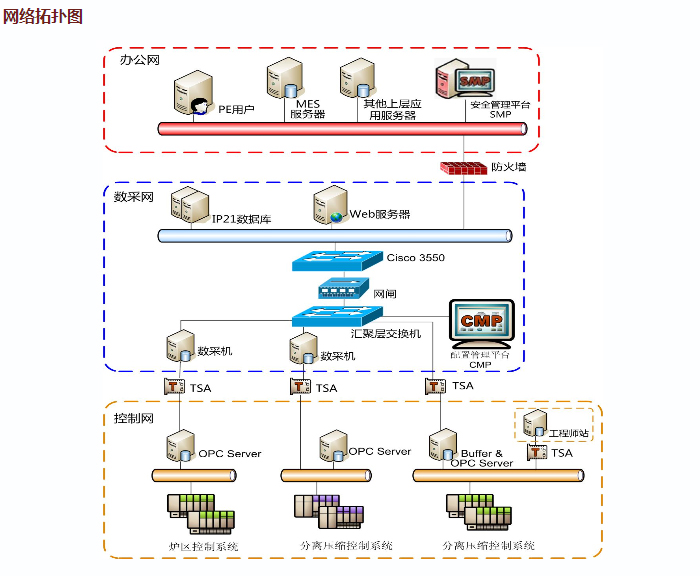
大多数企业模型化后的系统网络结构如上图所示
1、数采网与控制网之间的病毒相互感染隐患。虽然通过Buffer数采机或OPC Server的双网卡结构对数采网与控制网进行了隔离,部分恶意程序不能直接攻击到控制网络,但对于能够利用 Windows 系统漏洞的网络蠕虫及病毒等,这种配置并不起作用,病毒仍会在数采网和控制网之间互相传播。另外OPC通讯使用动态端口,无法使用常规防火墙进行防护。
2、来自工程师站的病毒扩散隐患。工程师站通常接入设备U盘、笔记本电脑等第三方,受到病毒攻击和入侵的概率很大,存在较高的安全隐患。
3、网络攻击事件无法追踪。网络中缺乏对网络进行实时监控的工具,一旦出现问题后,无法进行原因查找、分析和故障点查询。
工业防火墙用来分离安全系统网络与过程系统网络,实现关键系统与非关键系统的物理隔离。

与普通商用防火墙相比,工业防火墙更适于工业控制系统安全防护,主要体现在主要体现在:
(1)工业型:
参照ANSI/ISA-99 Standards的安全要求为设计理念,产品更具针对性和高效性,专门用于工业控制系统的安全保护。内置50多种专有工业通信协议,与常规防火墙不同的是,工业防火墙不仅是在端口上的防护,更重要的是基于应用层上数据包深度检查,属于新一代工业通讯协议防火墙,为工业通讯提供独特的、工业级的专业隔离防护解决方案。
具备在线修改防火墙组态功能,可以实时对组态的防火墙策略进行修改,而且不影响工业实时通讯。其它防火墙需要断电、重启等。工业型设计,导轨式安装,低功耗无风扇,具备二区防爆认证。
(2)独有专利安全连接技术:
首先防火墙自身是基于非IP的独有专利安全连接技术进行管理,能够阻挡任何欺骗式攻击。能够隐藏防火墙后端所有设备的IP地址,让入侵者无法发现目标,更无从谈发动任何攻击。集防火墙与虚拟路由于一身,能够像网络交通警察一样管控通讯网络数据通讯的路径、对象以及数据流的方向,可以设定数据流入、流出的单向或双向。
(3)实时网络通讯透视镜:
能够为目前控制网络故障分析、监控、记录提供一个简单、有效的可靠工具,能够确切的观察、分析、控制网络通信电缆中所使用的通讯协议、数据速度、访问对象等。实现对非法通信的实时报警、来源确认、历史记录,保证控制网络通讯的实时诊断。
(4) 满足 ANSI/ISA-99,IEC62443和 NERC-CIP 标准
根据 ANSI/ISA-99,IEC62443 和 NERC-CIP 标准, TSA 可以很方便的针对 PLC、 DCS、 RTU、IED 和 HMI 提供一个性价比很高的安全分区—一个配置得当的保护区域分组。
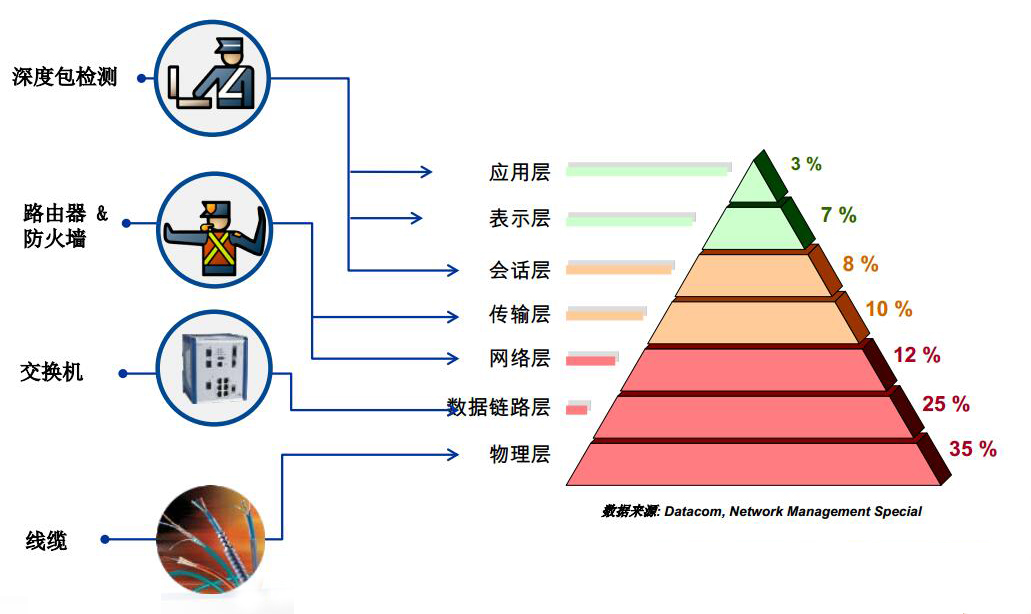
无论网络中任何位置发生攻击或者为人误操作,深度防护模型都可以有效的限制其对整个网络造成影响:
1、多层防护
2、差异化分层防护
3、针对特定威胁的分层防护
Contact Us
Building 6, Ningxing Jiali Plaza, No. 185 Mingxin Road, Yinzhou District, Ningbo City
Tel:( 86-574 ) 87861201
Fax:( 86-574 ) 87861200

Official Account

WeChat Channel
© 2021 JETRON Powered by www.300.cn 浙ICP备12043472号-1 SEO